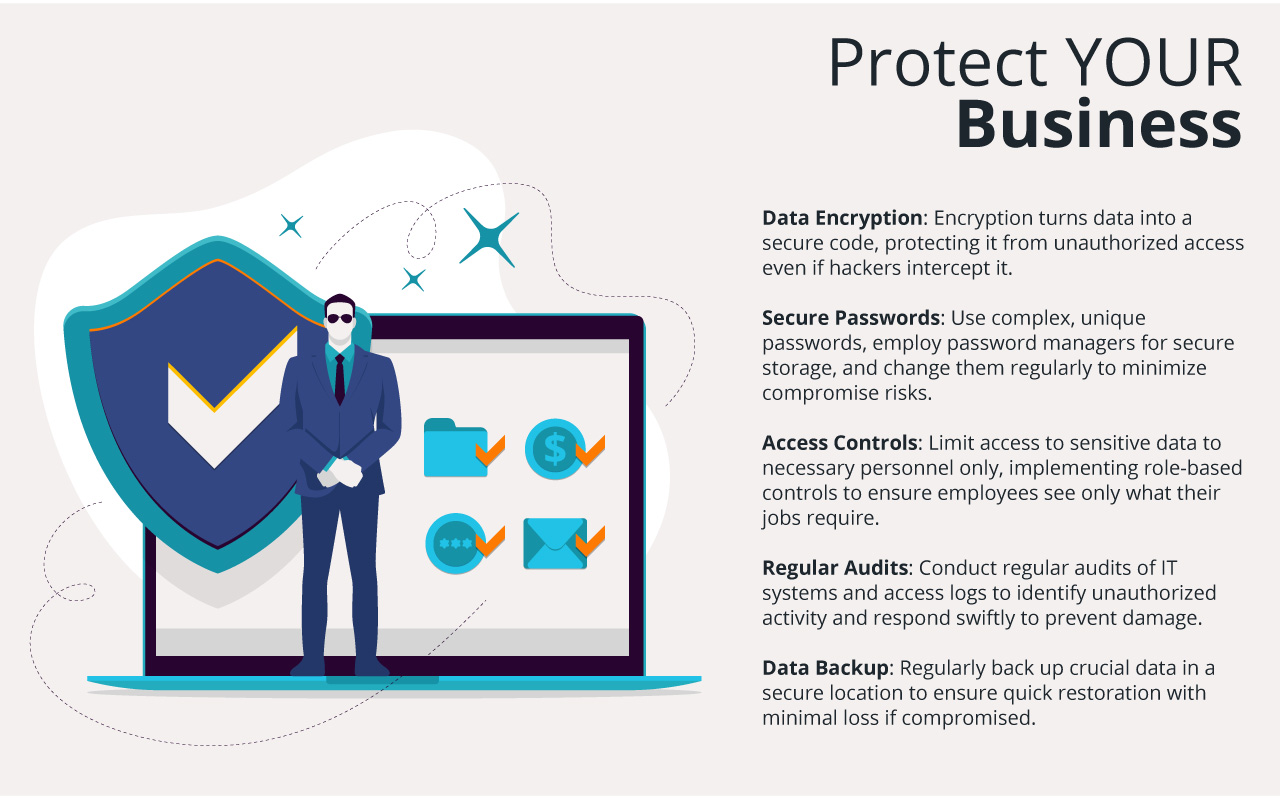
Cybersecurity is important for every business. Hackers are always looking for ways to steal data and disrupt operations. Fortunately, there are simple steps we can take to protect our business from these threats. Understanding and using
Continue ReadingCategory: Cybersecurity Best Practices
Simple Steps to Boost Cybersecurity for Your Business
Cybersecurity is important for every business. Hackers are always looking for ways to steal data and disrupt operations. Fortunately, there are simple steps we can take to protect our business from these threats. Understanding and using
Continue ReadingHow to Keep Your Business Safe from Online Threats
As businesses rely more on technology, the risk of cyber attacks grows. Cyber criminals aren't just targeting big companies; small and medium-sized businesses are also at risk. These attacks can lead to data breaches, financial losses,
Continue ReadingProtect Your Business with Strong Cybersecurity
Cybersecurity is more important than ever for businesses of all sizes. Cyber threats are constantly evolving, and protecting our sensitive data has become a critical task. Hackers are looking for any opportunity to exploit weaknesses in
Continue ReadingProtecting Your Data with Encryption Explained Simply
Protecting our data is more important than ever. With hackers constantly seeking ways to steal information, we must be vigilant. One effective way to keep data safe is through encryption. Encryption transforms our data into a
Continue ReadingUnderstanding Phishing Scams and How to Avoid Them
Phishing scams are becoming more common and sophisticated, targeting businesses and individuals alike. They typically involve tricking someone into giving away sensitive information like passwords, credit card numbers, or other personal details. These scams often come
Continue ReadingEasy Ways to Protect Your Company from Hackers
Every business, regardless of size, is at risk of being targeted by hackers. Cyber attacks can lead to stolen data, disrupted operations, and damaged reputations. Small businesses often think they won't be targeted, but hackers know
Continue ReadingMaintaining Security in the Cloud: Top Strategies for Protecting Your Data and Applications
In 2024, cloud adoption has become the norm for businesses of all sizes, seeking scalability, flexibility, and cost savings. As organizations transition their systems, applications, and data to the cloud, ensuring the security and privacy of
Continue ReadingHow Cybersecurity Compliance Can Protect Your Business from Legal Risks
Ensuring cybersecurity compliance is crucial in today’s business environment. As cyber threats become more advanced, businesses must adhere to regulations to protect their data and avoid legal consequences. Cybersecurity compliance involves following laws and guidelines that
Continue ReadingThe Importance of Regular Cybersecurity Audits for Businesses
As cyber threats become more sophisticated, regular cybersecurity audits are essential for businesses to stay protected. Without frequent audits, vulnerabilities can go unnoticed, exposing our systems and sensitive data. Regular audits allow us to identify and
Continue Reading