Cyber threats continue to evolve at a rapid pace, and one of the most alarming trends in 2025 is the rise of deepfake technology being used for cybercrime. Originally developed for entertainment and AI research, deepfakes
Continue ReadingCategory: Adaptive Security Approaches
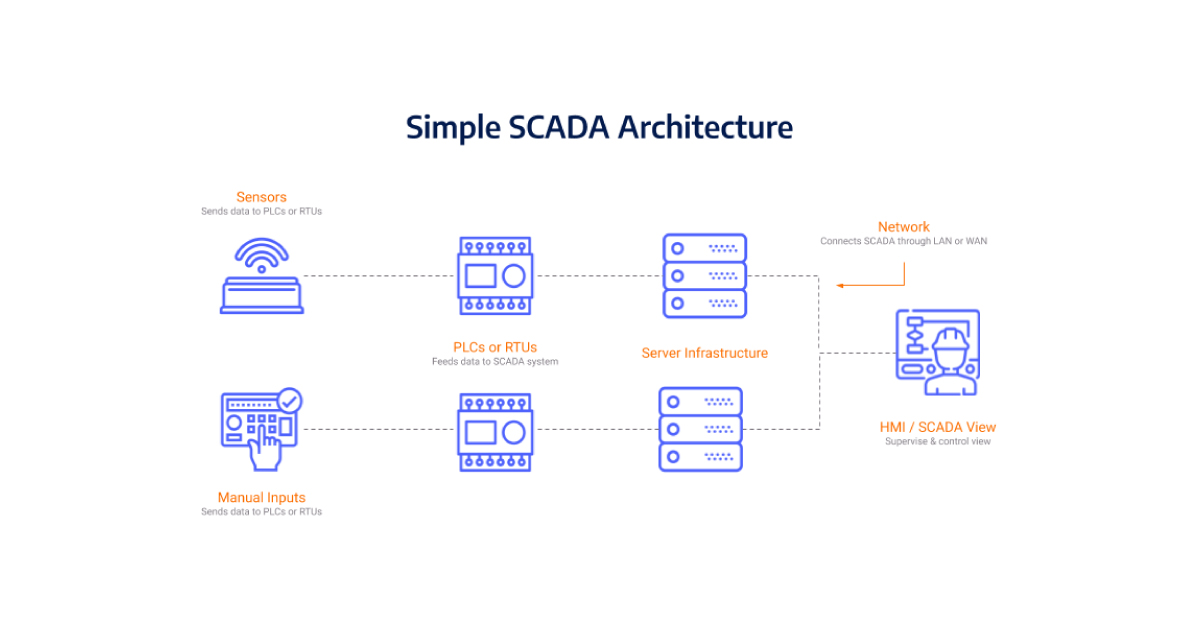
The Next Generation of SCADA Systems: Is SCADA Obsolete?
Supervisory Control and Data Acquisition (SCADA) systems have been the backbone of industrial automation for over three decades. Traditionally, these systems operated in isolated environments, making them relatively secure. However, with the integration of IT networks
Continue Reading- Adaptive Security Approaches
- Cyber Threat Intelligence
- Cybersecurity Best Practices
- Cybersecurity Training
- Risk Management
How to Identify and Mitigate Common Cyber Threats to Your Business
Cyber threats are a serious concern for all businesses now more than ever. Hackers are constantly evolving their methods, making it vital for us to stay ahead of these dangers. Identifying signs of cyber threats early
Continue ReadingEmbracing an Agile Cybersecurity Strategy: A Key to Business Resilience in 2024
As we move forward into 2024, business owners must remain vigilant and adaptable to stay ahead of the curve in the dynamic world of cybersecurity. The constant evolution of cyber threats, combined with rapid advancements in
Continue Reading