The Result of Maritime Cybersecurity Struggling to Catch Up: Cybersecurity Now Moving Up the Agenda For years, the maritime industry has lagged behind when it comes to cybersecurity—some estimates place it nearly a decade behind other
Continue ReadingAuthor: Carole Crawford
Building an Effective Incident Response Team for Cybersecurity
Incident response (IR) planning is essential for all industries, yet it's often neglected. Surprisingly, many organizations, regardless of their size or sector, lack comprehensive IR plans or fail to conduct regular exercises. Sometimes, IR planning is
Continue ReadingLeave No Stone Unturned: Maximizing the Reach of Your Pen Tests
Penetration testing is one of the most vital elements of any cybersecurity program. While once limited to evaluating network environments, the scope of pen testing has expanded dramatically alongside advancements in technology. From cloud computing and
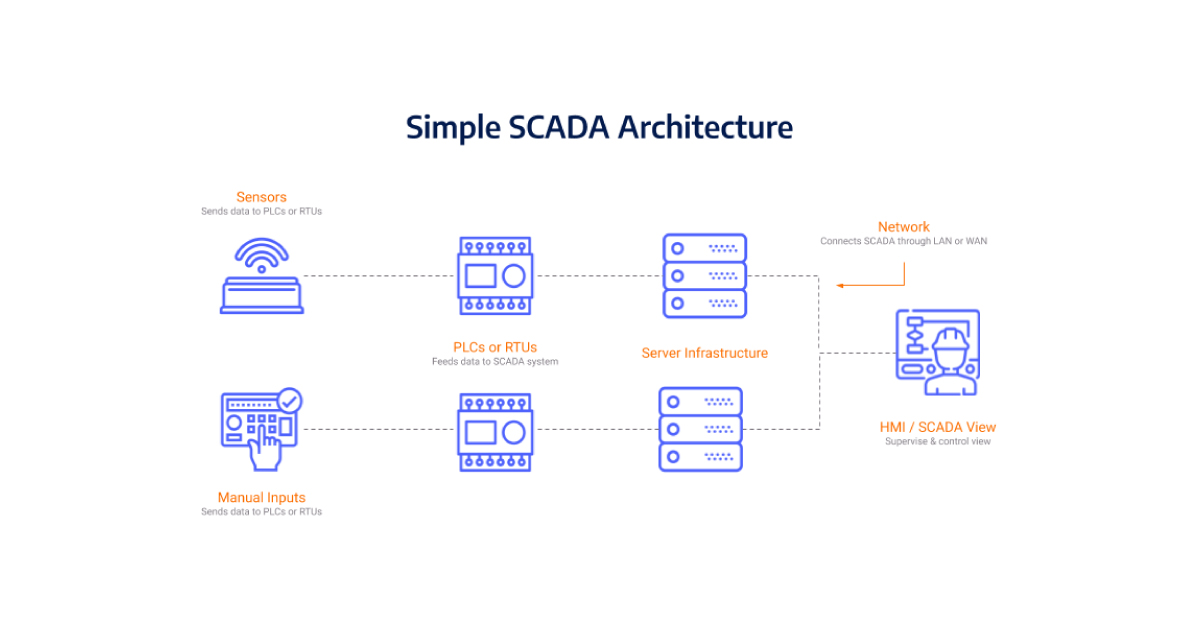
Continue ReadingThe Next Generation of SCADA Systems: Is SCADA Obsolete?
Supervisory Control and Data Acquisition (SCADA) systems have been the backbone of industrial automation for over three decades. Traditionally, these systems operated in isolated environments, making them relatively secure. However, with the integration of IT networks
Continue ReadingWhich Spyware Threats Are Affecting YOUR Industry?
Spyware is a silent but dangerous threat impacting numerous industries, especially those managing highly sensitive information. Technology companies, healthcare providers, defense contractors, and financial service firms are increasingly becoming prime targets. The sensitive nature of the
Continue ReadingThe Importance of Cybersecurity for Industrial Automation
The integration of operational technology (OT) with information technology (IT) has revolutionized industrial automation. Manufacturing plants and industrial facilities are now more efficient than ever, thanks to connected devices, SCADA systems, and advanced automation. However, this
Continue ReadingLessons Learned and Steps for a Secure New Year
We hope everyone had a joyful and relaxing Christmas break! As we gear up for New Year’s Eve and look forward to 2025, it’s the perfect time to reflect on this year’s cybersecurity lessons and ensure
Continue ReadingKeeping Your Business Safe This Christmas
The Christmas season is a time of celebration, but for cybercriminals, it’s the perfect time to strike. As businesses wind down, teams take vacations, and operations slow, attackers ramp up their efforts to exploit vulnerabilities. The
Continue ReadingCybersecurity Concerns for the HVAC Industry
The HVAC industry is experiencing rapid digital transformation, driven by the adoption of smart technologies and interconnected systems. While these innovations provide greater efficiency and convenience, they also expose HVAC companies to significant cybersecurity risks. From
Continue ReadingLearning about the Basic Cyber Safety Tips for Companies
Cyber safety is crucial for all companies today. No matter the size of the business, cyber threats are a constant concern. Hackers look for easy targets, and any business can fall victim if it doesn't take
Continue Reading