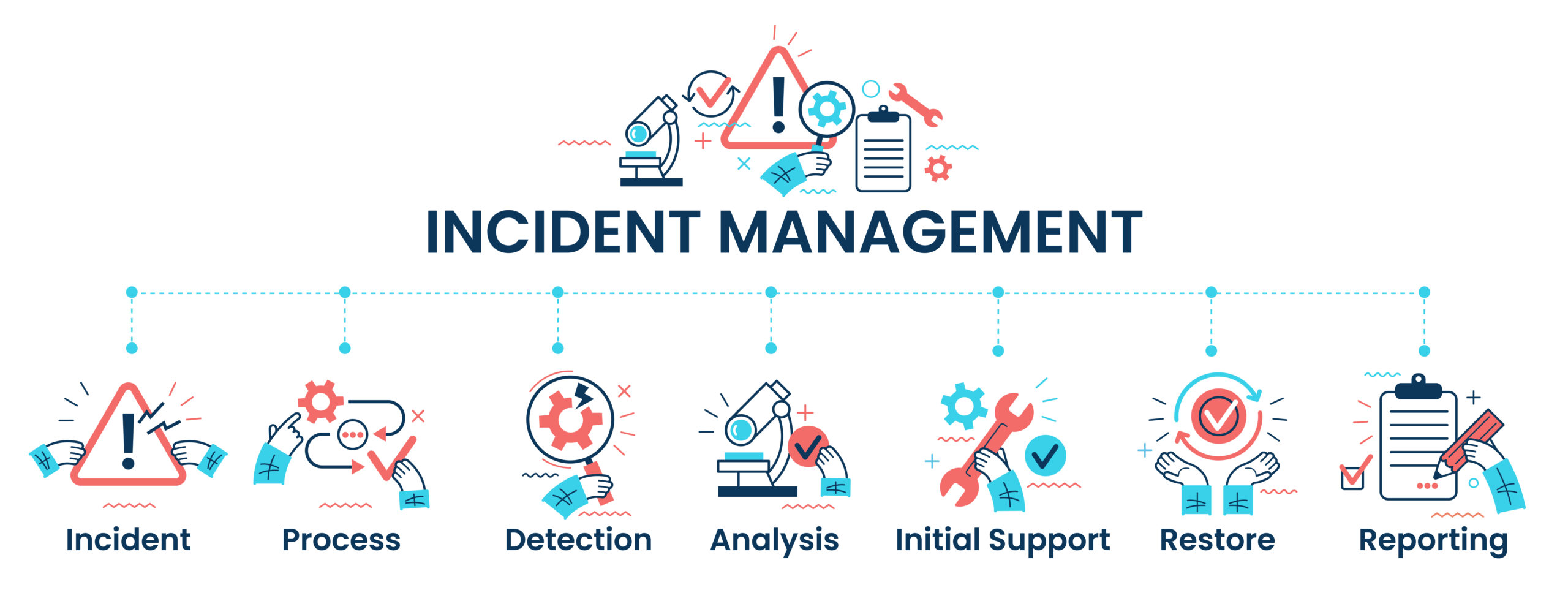
Incident response (IR) planning is essential for all industries, yet it's often neglected. Surprisingly, many organizations, regardless of their size or sector, lack comprehensive IR plans or fail to conduct regular exercises. Sometimes, IR planning is
Continue ReadingMonth: February 2025
- Cybersecurity Best Practices
- Incident Response
- Logistics Security
- Supply Chain Cybersecurity
- Warehousing
Strategic Logistics in 2025: Innovation, Resilience & Security
Are You Ready for an Effective Logistics Strategy in 2025? As we move further into 2025, many sectors within the logistics industry are struggling to keep pace with evolving strategies, automation advancements, and cybersecurity imperatives. While
Continue ReadingIIoT Cybersecurity Concerns for the Built Environment
Securing the Industrial Internet of Things (IIoT) in Built Environments The Industrial Internet of Things (IIoT) has revolutionized how industries manage automation, optimize resources, and make real-time decisions. Whether in HVAC systems, logistics, maritime operations, or
Continue ReadingDefending Against Deepfake Cyber Threats in 2025
Cyber threats continue to evolve at a rapid pace, and one of the most alarming trends in 2025 is the rise of deepfake technology being used for cybercrime. Originally developed for entertainment and AI research, deepfakes
Continue ReadingCloud-Based Intrusions in 2025: Key Lessons & Future Strategies
Now that we are well into Q1 of 2025, it’s crucial to reflect on recent trends in cloud security and adjust strategies accordingly. The cybersecurity landscape has dramatically shifted, and cloud-based threats have reached alarming new
Continue ReadingIs Your Logistics Strategy Ready for 2025?
As we move deeper into 2025, the logistics industry continues to evolve at an unprecedented pace. Companies are integrating automation, AI, and digital transformation to boost efficiency and remain competitive. However, while many are embracing innovation,
Continue Reading