The Growing Cybersecurity Challenge of IoT The Internet of Things (IoT) is transforming industries at an unprecedented scale. According to Forescout, by 2028, connected IoT devices will surpass 25 billion. While these devices enhance efficiency, they
Continue ReadingMonth: January 2025
Securing the New Remote Workforce: Cybersecurity Challenges & Solutions
The Cybersecurity Challenges of Remote Work With remote work now a permanent fixture for many businesses, cybersecurity professionals are facing increasing security incidents. A recent survey found that 66% of cybersecurity professionals have seen a rise
Continue ReadingPlaying Good Cop/Bad Cop: A Cautionary Tale About AI-Powered Tools
Artificial intelligence has revolutionized industries and opened doors to innovation and efficiency. However, as we embrace the benefits of AI, we must also be vigilant about the risks and vulnerabilities it introduces—especially when it comes to
Continue ReadingLeave No Stone Unturned: Maximizing the Reach of Your Pen Tests
Penetration testing is one of the most vital elements of any cybersecurity program. While once limited to evaluating network environments, the scope of pen testing has expanded dramatically alongside advancements in technology. From cloud computing and
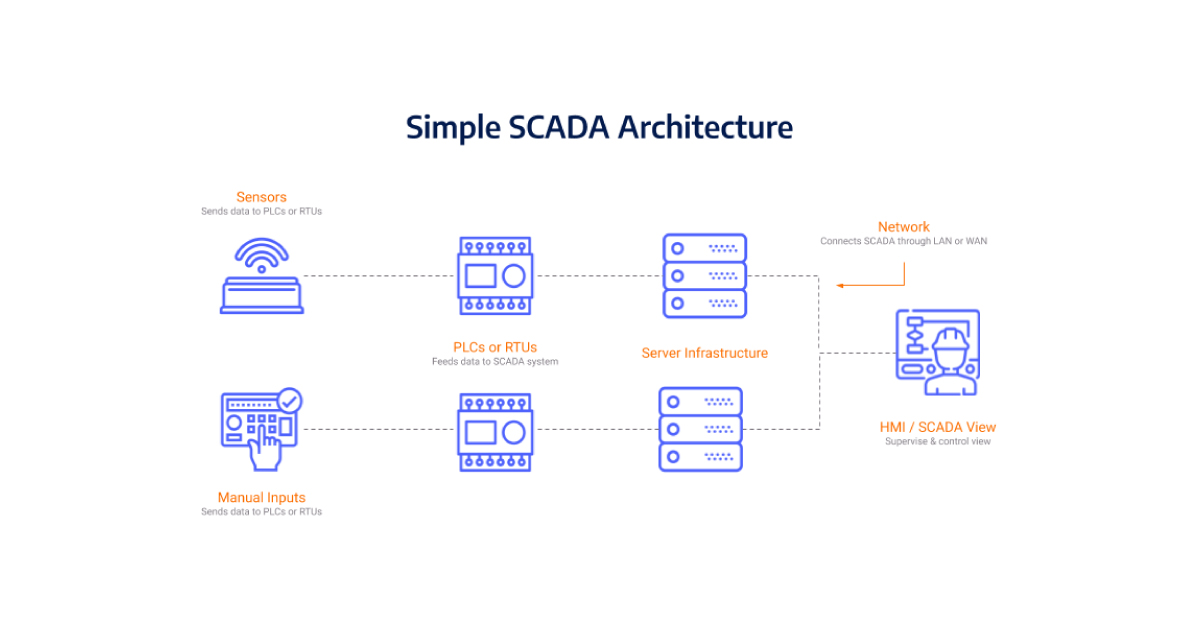
Continue ReadingThe Next Generation of SCADA Systems: Is SCADA Obsolete?
Supervisory Control and Data Acquisition (SCADA) systems have been the backbone of industrial automation for over three decades. Traditionally, these systems operated in isolated environments, making them relatively secure. However, with the integration of IT networks
Continue ReadingWhich Spyware Threats Are Affecting YOUR Industry?
Spyware is a silent but dangerous threat impacting numerous industries, especially those managing highly sensitive information. Technology companies, healthcare providers, defense contractors, and financial service firms are increasingly becoming prime targets. The sensitive nature of the
Continue ReadingThe Importance of Cybersecurity for Industrial Automation
The integration of operational technology (OT) with information technology (IT) has revolutionized industrial automation. Manufacturing plants and industrial facilities are now more efficient than ever, thanks to connected devices, SCADA systems, and advanced automation. However, this
Continue ReadingHow to Build a Strong Cyber Defense for Your Business
Building a strong cyber defense is crucial for keeping your business safe from cyber threats. Cyber attacks can cause a lot of damage, from stealing sensitive information to disrupting operations. A robust cyber defense helps protect
Continue ReadingMaritime Cybersecurity in 2025: Addressing Security Gaps and Risks
The maritime industry has undergone tremendous changes in recent years, driven by the need to digitize, automate, and upgrade systems to stay competitive. Yet, as we approach the end of 2025, this industry remains a critical
Continue Reading