Cybersecurity is not just a technicality but a foundational component of any successful business operation. As we continue to integrate more sophisticated technologies into our daily workflows, the complexity of our cyber environments increases. This escalation requires a robust cybersecurity framework to effectively manage and mitigate risks associated with cyber threats. For businesses, understanding and implementing such a framework is no longer optional but a necessity for securing organizational assets and maintaining customer trust.
A comprehensive cybersecurity framework serves as a blueprint for managing and reducing cybersecurity risks in a structured and scalable manner. It aligns security efforts with business requirements, risk tolerances, and resources within the organization. In 2024, as cyber threats evolve and become more complex, tailoring your cybersecurity practices to address these new challenges is crucial. This involves not only updating defenses but also ensuring that they are adaptable and resilient against the sophisticated and constantly changing threat landscape.
Whether you’re a startup, a small business, or a large corporation, the urgency to adopt a holistic and proactive approach to cybersecurity is universal. Through this discussion, we aim to guide you in understanding the vital components of an effective cybersecurity framework and how you can optimize it to strengthen your organization’s defense mechanisms against emerging cyber threats.
Understanding the Basics of a Cybersecurity Framework
In today’s digital age, the significance of having a robust cybersecurity framework cannot be overstated. As we navigate through various threats in the cyber world, establishing a strong framework is akin to laying the foundation of a fortress for your business’s digital assets. A cybersecurity framework offers a structured approach, encompassing policies, guidelines, and controls designed to manage the risks associated with IT and information security. It helps us identify our key assets, assess our vulnerabilities, and respond to cybersecurity incidents effectively. By incorporating industry standards and best practices, we can ensure that this framework not only meets our specific needs but also complies with legal and regulatory requirements. It serves as the first line of defense, integral in safeguarding our operations from emerging cyber threats.
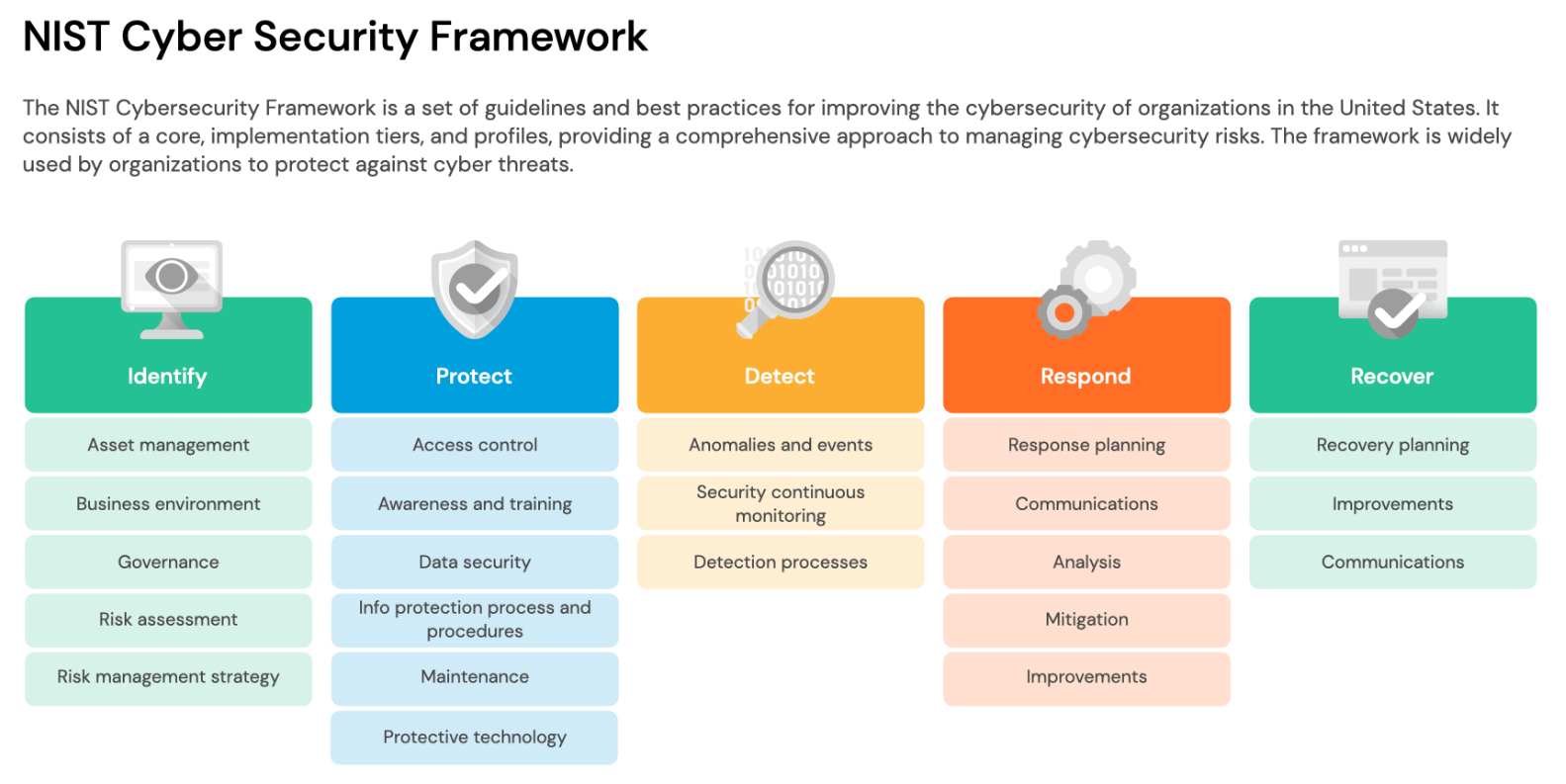
Key Components of an Effective Cybersecurity Framework
When developing an effective cybersecurity framework, understanding its key components is crucial to ensure comprehensive coverage of all security aspects. Here’s an outline of the essential elements:
1. Identifying Assets and Risks: A thorough inventory of all digital assets and an assessment of their respective vulnerabilities. This forms the base upon which the rest of the framework is built.
2. Protecting The Infrastructure: Implementing appropriate safeguards such as firewalls, antivirus software, and encryption mechanisms to protect the integrity of our data and networks from unauthorized access and attacks.
3. Detecting Intrusions: Deploying advanced monitoring systems and techniques to swiftly identify irregular activities or potential breaches within the system, allowing for immediate response before any significant damage is inflicted.
4. Responding to Incidents: Establishing a procedure for incident response that includes notifying stakeholders, containing and mitigating risks, and learning from the attack to bolster future defenses.
5. Recovering Post-Breach: Formulating a recovery plan to restore any capabilities or services impaired by a cybersecurity incident while maintaining transparency with customers and partners.
By focusing on these fundamental elements, we can create a cybersecurity framework that not only responds effectively to threats but also aligns seamlessly with the structure and strategy of our organization. This framework ensures that our defenses evolve parallel to changing cyber threats, helping safeguard our valuable assets, and maintaining trust with our clients and stakeholders.
Steps to Optimize Your Cybersecurity Framework for Maximum Protection
To ensure our cybersecurity framework provides maximum protection, we must actively optimize and adapt it to the evolving digital landscape. Optimizing a cybersecurity framework involves a continuous process of assessment, adjustment, and improvement, focusing on both preventive measures and rapid response capabilities. The initial step is to systematically review all existing security measures and compare them to the best practices in the industry. We must scrutinize the alignment of our security strategies with our business objectives, ensuring that every policy and procedure contributes effectively to the overarching goal of enterprise security.
Next, we integrate advanced technological tools and services that enhance our threat detection and response times. By employing machine learning algorithms and AI-driven analytics, we can preemptively identify potential threats and vulnerabilities, enabling proactive rather than reactive management. Furthermore, it’s imperative to ensure that our team is well-trained and versed in the latest cybersecurity threats and mitigation strategies. Regular training sessions, simulations, and drills keep our staff sharp and prepared, turning them into an active component of our cybersecurity defenses. By advancing our tools, strategies, and team capabilities, we elevate our cybersecurity framework to provide robust, resilient protection tailored precisely to our needs and threats.
Evaluating and Maintaining Your Cybersecurity Framework
Evaluating and maintaining your cybersecurity framework is crucial for ensuring that it remains effective against current and future threats. Regular evaluation helps to identify gaps in the protection that might have surfaced over time or due to changes in our business environment or technology landscape. We conduct comprehensive audits and reviews quarterly, involving external experts to provide an unbiased assessment of our cybersecurity measures. This evaluation includes testing our recovery and response plans through controlled breach simulations and examining the effectiveness of our incident response strategies under realistic pressure scenarios.
Maintenance involves regular updates to our security practices and technologies. As part of this commitment, we keep all software and systems up to date with the latest security patches and upgrades, thus mitigating risks that come from vulnerabilities in outdated systems. Additionally, we revisit our risk assessment models and update them to reflect new business processes or external threats, ensuring a holistic and updated approach to organizational security. In essence, the ongoing evaluation and vigilant maintenance of our cybersecurity framework foster a security-first culture within our organization, critically reducing our risk profile and enhancing our ability to operate with confidence in a digital world.
Conclusion
In conclusion, adopting and maintaining a dynamic cybersecurity framework isn’t just about safeguarding data—it’s about ensuring the continuity and success of our business. We recognize the critical need for robust cybersecurity measures in today’s digital age. Effective management of cyber risks is integral to both operational stability and strategic confidence. By continuously optimizing and rigorously evaluating our cybersecurity practices, we protect our assets and stakeholders and enable our business to thrive in an increasingly digital marketplace.
If cybersecurity is a growing concern for your business, don’t wait to take action–contact Saturn Partners to schedule a consultation. We are dedicated to helping you develop customized cybersecurity services that not only meet but exceed industry standards for safety and compliance. Let us help you secure your operations, protect your assets, and achieve peace of mind in the digital age.